Microsoft Tops List of Most Impersonated Brands in Phishing Attacks
Check Point Research finds Microsoft at 36% of Q1 2025 phishing lures, followed by Google and Apple—underscoring urgency of user vigilance and brand safeguards.
A new Check Point Research report has revealed that Microsoft is the most imitated brand in phishing attacks during Q1 2025, accounting for 36% of all lures. With criminals weaponising trusted names to steal credentials and financial data, the study underscores the critical need for both consumer awareness and enterprise-grade email security measures.
Rise of Brand-Based Phishing
Phishing remains the top cyber threat vector, and the report shows brand impersonation as the favoured tactic. Attackers craft emails and spoofed websites mirroring real domains, often leveraging genuine logos, fonts, and language, to trick targets into revealing passwords or installing malware.
Top 10 Most Impersonated Brands
Check Point’s findings rank the leading brands spoofed in Q1 2025:
-
Microsoft – 36%
-
Google – 12%
-
Apple – 8%
-
Amazon – 4%
-
Mastercard – 3%
-
Alibaba – 2%
-
WhatsApp – 2%
-
Facebook – 2%
-
LinkedIn – 2%
-
Adobe – 1%
The tech sector led the pack, followed by social networks and retail.
Spotlight on Microsoft and Mastercard Schemes
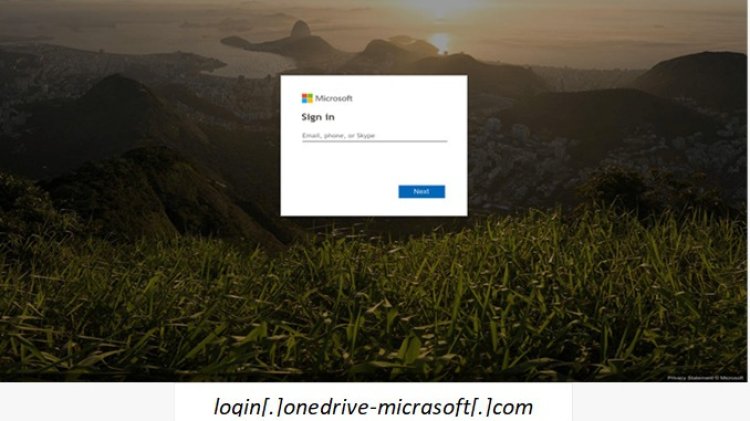
Microsoft’s dominance stems from credential-harvesting campaigns disguised as OneDrive or Office 365 alerts—complete with fake login pages (e.g., login.onedrive-micrasoft.com). Notably, February saw a surge in Mastercard phishing websites targeting Japanese users, masquerading as official banking portals to extract card numbers and CVVs.
Expert Insights and Consumer Guidance
Omer Dembinsky, Check Point’s Data Research Manager, warns: “Phishing leveraging trusted brands will remain rampant. Businesses must deploy multifactor authentication and real-time link scanning, while users should err on the side of scepticism, verifying URLs and contacting providers directly.”
Enterprise Safeguards
Organisations are urged to combine technical controls, DMARC enforcement, sandboxed email attachments, and AI-driven anomaly detection with ongoing user-education programs. Simulated phishing drills can maintain employee vigilance, reducing click-through rates and potential breaches.
The Road Ahead
As brands accelerate cloud-service adoption, their digital footprints expand, presenting more spoofing opportunities for threat actors. Check Point recommends a layered defense: brand-protection services that monitor newly registered domains, plus endpoint solutions that flag credential-theft behaviors.
Final Thoughts
Microsoft’s position as Q1 2025’s top phishing target highlights a broader epidemic: impersonation of highly trusted names. By combining robust email protections, proactive domain monitoring, and continual user training, both enterprises and individuals can fortify their defences, turning the tide on credential-stealing syndicates.












